Overview
- This article will introduce the basic configuration of IPS in Sophos XG Firewall run version 18 firmware.
- I know than Intrusion Detection System and Intrusion Prevention System are different type of protection, but in sophos I only found IPS as you mentioned. In Fortinet you can deploy in mirroring mode for function as IDS, in CheckPoint there are a module that can be deployed as a IPS or as a IDS (called IPS-1) in mirroring mode too.
- Sophos XG Firewall provides intrusion prevention, advanced threat protection, cloud sandboxing, dual AV, Web and app control, email protection and a full-featured Web application firewall.
- The EICAR test string is not a virus, it is an industry-standard detection test. Sophos Anti-Virus will report its presence as EICAR-AV-Test virus. Download the eicar string from the eicar website. Copy the string into a notepad and save it as eicar.txt.
- Since upgrading the firmware to the latest version 9.312-8 my internet performance has fallen massively. I have a Gbit connection to the internet and with Intrusion prevention turned on, I get anything from 10mbit to 100mbit depending on number of users.
What does it have ?
Sysmon from Sysinternals is a substantial host-level tracing tool that can be help in detecting advanced threats on your network. In contrast to common Anti-Virus / Host-based intrusion detection system (HIDS) solutions, Sysmon performs system activity deep monitoring, and log high-confidence indicators of advanced attacks.
1. DoS Attacks
Attack Type
- Displays the attack type: SYN Flood, UDP Flood, TCP Flood, ICMP Flood and IP Flood.
Source
- Displays whether source packet control is applied or not. If applied, it indicates the number of packets dropped.
Destination
- Displays whether destination packet control is applied or not. If applied, it indicates the number of packets dropped.
Click the name of the attack type you want to view to get real time updates on flooding.
2. IPS Policies
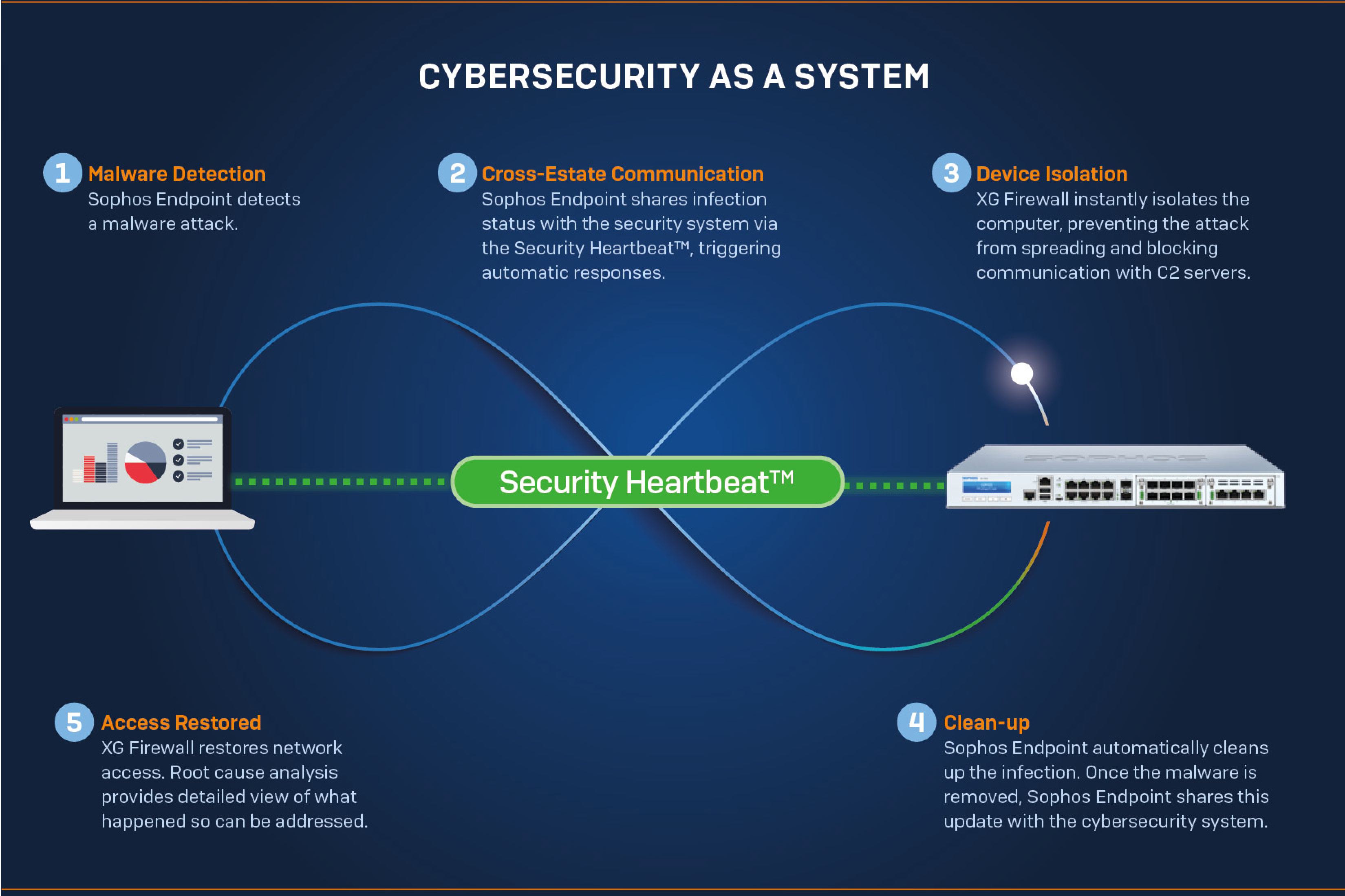
The device is a real time Intrusion Prevention System (IPS) system that protects your network from known and unknown attacks by worms and viruses, hackers and other Internet risks.
The device at the perimeter of your network analyzes entire traffic and prevents attacks from reaching your network. Whether it is a worm, a suspicious web request, a hacker targeting your mail server or any other attack – it simply does not get through.
- Intrusion Prevention System module is a subscription module that needs to be subscribed before use.
- You can also view and manage the IPS status on the Monitor & Analyze > Diagnostics > Services page.
IPS consists of a signature engine with a predefined set of signatures. Signatures are the patterns that are known to be harmful. IPS compares traffic to these signatures and responds at a high rate of speed if it finds a match. Signatures included within the device are not editable.
As per your network requirements, device allows you to define multiple policies instead of one global policy, to decrease packet latency and reduce the false positives.
IPS policy allows you to view predefined signatures and customize the intrusion prevention configuration at the category as well as individual signature level. Categories are signatures grouped together based on the application and protocol vulnerabilities.
The device instead of providing only a single policy (global) for managing multiple networks/hosts, allows to tailor policy per network/host i.e. allows to define multiple policies for managing multiple networks/hosts.
To enable the Intrusion Prevention System, apply IPS policy from Security Policies. You can create rule to apply:
- Single policy for all the users/networks
- Different policies for different users/networks or hosts.
As Security Policies control all traffic passing through the device and decide whether to allow or drop the connection, IPS rule will be applied to only that traffic/packet which passes through Firewall.
2.1 Category
Signatures are organized in categories such as DNS, Finger, P2P, DDOS, and others. These signature categories are listed in the policy. You can configure these categories to change the prevention and/or detection settings. To perform Intrusion Prevention, you need to enable IPS services for each category i.e. you will be able to configure attack threats for individual signature only if an IPS service for the category is “Enabled”.
IPS provides six actions for managing attack threats: (action if signature matches)
- Allow Packet – Allows the packet to its intended destination.
- Drop Packet – Drops packets if detects any traffic that matches the signature.
- Disable – Disables the signature, if it detects any traffic that matches the signature.
- Drop Session – Drops the entire session if detects any traffic that matches the signature.
- Reset – Resets entire session if detects any traffic that matches the signature.
- Bypass Session – Allows the entire session if detects any traffic that matches the signature.
The device provides following pre-defined policies. You can directly use policies 1 to 6 without any modifications while policies 7 to 10 can either be used directly or, can be modified as per your requirements:
- 1. DMZ TO LAN
- 2. DMZ TO WAN
- 3. LAN TO DMZ
- 4. LAN TO WAN
- 5. WAN TO DMZ
- 6. WAN TO LAN
- 7. generalpolicy
- 8. lantowan strict policy
- 9. lantowan general policy
- 10. dmzpolicy
2.2 Create an IPS policies
Go to Protect > Intrusion Prevention > IPS Policies and click Add.
Specify the following:
Name
- Enter a unique name for the IPS policy.
Description
- Enter a description for the IPS policy.
Clone Rules
- Select the IPS policy to be used as a template from the available list.
Available Options:
- generalpolicy
- lantowan_strict
- lantowan_general
- dmzpolicy
- LAN to WAN
- LAN to DMZ
- WAN to DMZ
- WAN to LAN
- DMZ to WAN
- DMZ to LAN
Click Save.
Note : Once the policy is created, policy rules can be added to take appropriate action for signatures in the policy. Define a rule to configure an action to be taken when the matching traffic pattern is found. If the rules are already added, a list of rules is displayed along with its details like signature filtering criteria, action.
2.3 Edit IPS Policies
To edit IPS policies go to Protect > Intrusion Prevention > IPS Policies.
Click on the pencil icon to the right of the IPS policies we just created.
After click Edit list of signatures appear, click pencil icon to Edit the signature, click Trash icon to Delete Signature out of list and click Add to Add new signature.
Note: The rules available in the list are clone from the LAN TO WAN Policies that we selected earlier so editing them will not affect the original LAN TO WAN Policies.
3. Custom IPS Signatures
Custom IPS Patterns provide the flexibility to customize IPS for diverse network environments. Predefined IPS patterns included in the device cover common attacks while Custom IPS Patterns protect your network from uncommon attacks that are due to the use of proprietary server, custom protocol, or specialized applications used in the corporate network.
Administrator can create Custom IPS Pattern and configure policies using them. However, the IPS scanning will be effective only if Network Protection module is subscribed.
3.1 Add IPS Pattern
Go to to Protect > Intrusion Prevention > Custom IPS Signatures and click Add.
Enter the IPS Signature details.
Name
- Enter a name to identify the Custom IPS Signature.
Protocol
Select IPS protocol from the list.
Available Options:
- TCP
- UDP
- ICMP
- ALL
Custom Rule
Specify IPS Signature definition.
Signature definition must begin with a keyword followed by the value enclosed between the double quotes and must end with semicolon (;)
Format: Keyword: “value”;
For example, content: “USER JOHN”;
If traffic with the content USER JOHN is detected, action defined in the policy will be taken.
Refer to Appendix B – IPS – Custom IPS Pattern Syntax for more details on creating IPS Pattern.
Severity
Select the level of severity from the available options.
- Critical
- Major
- Moderate
- Minor
- Warning
Recommended Action
Specify action to be taken on the selected policy when matching pattern is found.
Available Actions:
- Allow Packet – Check each packet before taking action.
- Drop Packet – Drop packets.
- Drop Session – Terminate entire session instead of scanning all the session packets to save resources and avoid getting high number of alerts.
- Reset – Send TCP reset packet to the originator.
- Bypass Session – Scan initial packets only. If the initial packets match the pattern then the rest of the session packets are not scanned and the traffic is allowed to pass.
In all the cases, device generates the log and alerts the Network Administrator.
Click Save.
YOU MAY ALSO INTEREST
Introduction
At my home, I have a dedicated SuperMicro 1U server running Sophos UTM 9 version 9.355-1. I call it my router, buy it is a router, a firewall, a web proxy, an intrusion detection device and much more. All of this, free. It is an excellent product. If you don’t have it, you can see for yourself. They sell devices with the software on it, but you can also download a CD image or virtual drives to install it on a virtual machine.
On this device, i configured the “Web Filtering service” to act as a proxy. As I have a domain, I configured a GPO to push the windows proxy settings to all my computers joined to the domain. Finally, I configured a server in “Authentication Services” to make the device join my domain and use it to synchronise the domain users for the proxy authentication.


The Problem
All went fine, really fine. I have a lot of statistics concerning the internet usage on my network. I can select hundreds of web site categories and decide to block them, allow them or put a quota on it. I can also configure fancy rules to decide what I allow to go through and what I want to block.
The problem I had is, OneDrive could not get through. The first symptoms was with my OneNote notebooks I share with OneDrive, they were not able to synchronize. The first error, indicating a synchronisation error with a 0x80004005 error code and another saying he needed the password with a 0xE4010668 error code. As these errors disappeared as soon a I deactivated the proxy, I knew I had to create an exception rule.
Sophos Intrusion Detection
On the Sophos device, there is a multitude of exceptions already configured in the “Web Protection / Filtering Options / Exceptions” section. I did some Google Fu, found some posts who guided me, but nothing to solve my problem.
Sophos Xg Intrusion Detection
The first circle of hell I encountered is, Sophos says the rules can specify URL based on regular expressions. I spent half an hour examining URLs rejected by the proxy who looked related to OneDrive and built tested regular expressions and pasted them in my exception rule but there was no effect. So, I spend another ten minutes trying to find why they were ignored.
A Way Out
As I found out, I had to use expressions based on regular expressions, not real regular expressions. For exemple, an expression to let through “https://my.domain.com” could be “^https:[/][/]my[.]domain[.]com[/]“, or “^https://my.domain.com/“. But for Sophos, it should be “^https://my.domain.com/“… I found out by examining already configured rules. Knowing that, google brought me the details for building a valid expression. I then transformed them and generated my exception rule, adding URL expressions one by one until my OneNote was able to sync and my OneDrive folders also.
Follow The Dotted Line
- In the WebAdmin page of Sophos UTM, go to “Web Protection”, then “Filtering Options”.
- Press the “New Exception List…” button.
- Give a name to the exception, I used “OneDrive”, and check all the following check-boxes. Maybe I should have left some alone, but in my opinion, I can leave everything open concerning OneDrive.
- In the “For all requests” section, select “Matching these URLs” and add the following expressions.

^https://[^.]*.hotmail.com/ ^https://[^.]*.storage.live.com/ ^https://[^.]*.docs.live.net/ ^https://onedrive.live.com/ ^https://[^.]*.officeapps.live.com/
- Save this and activate the rule by turning the switch on.
- Let a few seconds for Sophos to refresh his rules list and resync your OneNote and/or OneDrive.
Update – 2016.04.05
In a report, I have seen there is a “Personal Network Storage” category in the pre-configures filtered URL categories. I thought I would not need my custom filter if I disable this category from the filter, but I was wrong.
I disabled my custom filter and unchecked the “Personal Network Storage” from the list of blocked categories. I then tried to synchronize my OneNote notebooks and it didn’t work.
So, I left the “Personal Network Storage” category unchecked and activated my custom filter.
To find this category and uncheck it, in the WebManager interface, go to “Web Protection”, “Filtering Options” section and then in the “Categories” tab. Go to the “Private Homepages” item, click “Edit” and you will see it there.
